Report from Néosoft on December 19th, 2023
The text below is a summary of the security audit performed by Néosoft. See the full report.
AUDIT R-YOGI PLUGINS - Detailed Report - v1.0.pdf
Introduction
This document reports the security audit results of the Confluence and Jira plugins “Requirement Yogi Cloud” and “Requirement Yogi for Jira Cloud” developed by the company Requirement Yogi.
Néosoft did the audit between for a week in December 2023.
Requirement Yogi provided three accounts: Super Admin, Admin and User.
N.B: the results come from 4 days of audit. Thus, they may be only a subset of what an attacker with no time limit can find.
Risk analysis summary
The main risks which the auditor was asked to focus on were:
-
Data injection,
-
Security Misconfiguration.
During the audit, the auditor has determined two scenarios that could impact the company Requirement Yogi:
-
It is possible to export data in Excel format. However, malicious users (including those with "user" profile) could deliberately enter malicious Excel formulas in these data in order to execute arbitrary code on the workstations of people downloading them. A security warning will probably be displayed when Excel is opened, but most users ignore these warnings.
-
The Swagger of the plugin is accessible without authentication at the Swagger URL.
Risk assessment grades
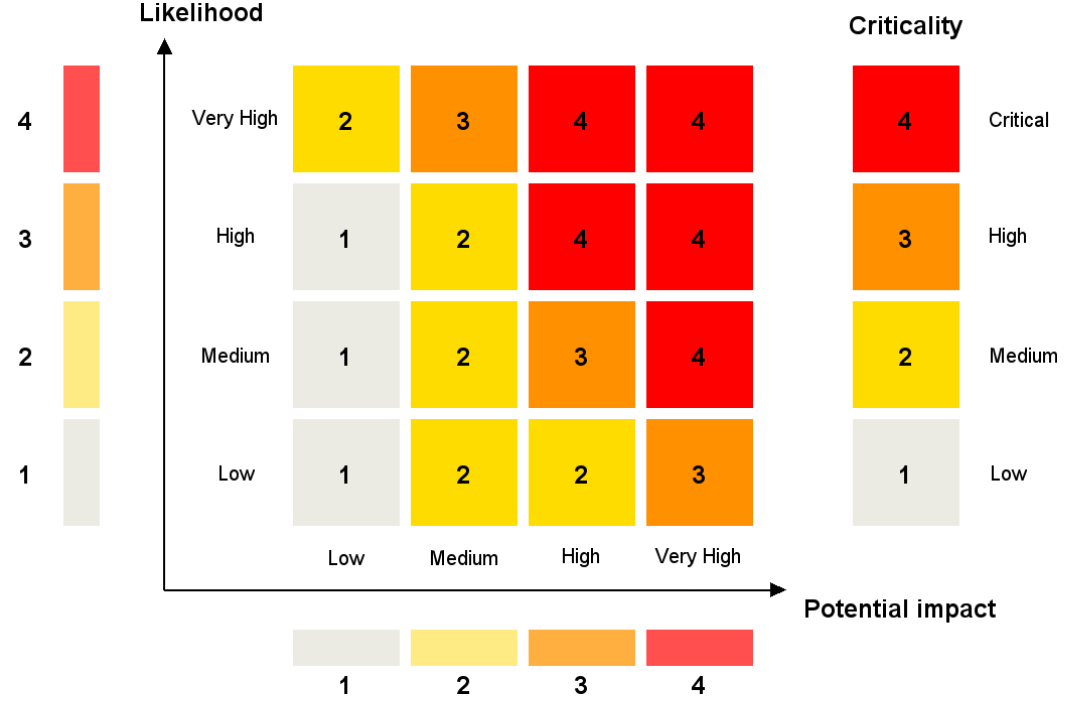
Summary
|
Scenario |
Likelihood |
Impact |
Criticality |
Action to lower the risk |
|---|---|---|---|---|
|
Excel formula injection |
2 |
2 |
2 |
Filter Excel formulas in exported files |
|
Access to the swagger file |
1 |
1 |
1 |
Advised : Filter access to the Swagger
|
General overview
Strength
✓ Very limited potential attack surface
✓ Very few audit findings
✓ Non-critical audit findings
✓ Very quick fixes proposed
✓ JWT session tokens well signed / secured
✓ Security good practices generally taken into account
Possible improvements
❖ Excel formula injection in exportable data
❖ Access to Swagger documentation without authentication
Conclusion
During the audit, no critical or high vulnerabilities were found by the auditor.
By focusing on the security picture only, the plugin Requirement Yogi Cloud is at a good level.
An attacker will certainly take a considerable amount of time to find and exploit a potential vulnerability in the API. Thus, an attacker would try gaining access to the system by other meanings, like stealing the AWS credentials, doing a phishing attack on employees or other.
The global security score assigned to the service is A, meaning that no critical vulnerability has been identified.
Two audit findings have been reported, one of which is more a recommendation for improvement than a real vulnerability.
Malicious users could deliberately enter malicious Excel formulas in exportable data to execute arbitrary code on the workstations of people downloading them. A security warning will probably be displayed when Excel is opened, but most users ignore these warnings.
The main risk would therefore be to use the application as an attack vector to compromise other users' workstations, to steal the data stored on them, or possibly to increase one's privileges on the application.
Grade : A
No significant vulnerability or very uncritical vulnerabilities
